What happened to Twitter?
Twitter has disclosed that hackers targeted about 130 accounts during the cyber attack last mont, an incident in which profiles of many prominent personalities and organisations were compromised. Hackers had accessed Twitter’s internal systems to hijack some of the platform’s top voices used them to solicit digital currency. Among those targeted were US presidential candidate Joe Biden, reality TV star Kim Kardashian, former US President Barack Obama and billionaire Elon Musk and used them to solicit digital currency. It is believed that the the apparent scammers received more than €87,000/$100,000 worth of cryptocurrency.
What is Phishing?
“Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.” – Phishing.org
In layman’s terms phishing is tricking someone into thinking you’re someone you’re not in order to gain sensitive information from them. The term phishing was coined in 1996 by a group of hackers who were “fishing” for passwords in the ocean that is the web. So phishing has been around for a long time and a lot of time is easily noticeable to people who are used to being on the internet but there are often cases when it’s not easily noticeable because it is so well executed or often not where you were expecting it to be.
An example of phishing on a personal level to provide some understanding of how well it can be done was a time I looked to purchase a car. I was browsing online and came across a very reasonable car on DoneDeal (too reasonable) so I sent a message to the owner. They replied promptly with a long winded message about how they were moving away and that’s why they were selling the car, they said they had already moved and the car would be transaction and shipping would be by eBay (this may all seem strange and suspect but I’d looked around and it was commonplace for eBay to ship the cars, handle the transaction etc.).
They sent me a link to purchase on eBay and when I clicked on the link it was perfect, it looked exactly like eBay, all the buttons and search function worked etc. The only thing that was a miss was that the URL said ebay.com which was fine, but it was the part after the .com that was the issue which can be seen below. I did some digging, emailed eBay and DoneDeal and sure enough it was a fake ad with replicated landing page of eBay which if I had entered my details would have been stolen.
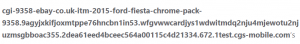

What does any of this have to do with Twitter?
Good question, the reason for the long winded explanation of phishing is because that is exactly how Twitter one of the largest social media which boasts 330 million users according to Statista was hacked. The exact details of how what happened are still yet to be announced but what is known is that using a phone spear phishing scam the hackers socially engineered certain Twitter staff members to hand over their credentials which provided them with access to Twitters internal system.
The initial staff compromised did not have access to the accounts that were hacked but once the hackers were within the system, they were able to gain control of staff members credentials that did have access. This is the key point to the whole hack the people who got hacked were relatively low down within the company’s structure but by them being compromised it allowed for this major attack to happen.
It’s not just scamming people out of money that was the issue in this instance. Firstly, these individuals were able to access the internals of Twitters systems which poses the question what more could they have done? Secondly, the people who had their accounts compromised also had their data downloaded and personal messages accessed in some instances. Now it’s unlikely that high profile individuals would store anything secretive in Twitter DM’s but it’s the principle that personal information could be compromised in what is meant to be a secure medium due to no fault of their own.
ReganStein offers comprehensive Cyber Security solutions for companies to ensure their safety. Learn more about what we offer here.
At the time of writing all facts were correct, as this is an ongoing investigation some elements of this article may change over time.


